In the present advanced age, cybersecurity threats are continually developing, with Distributed Denial of Service (DDoS) attacks being one of the most predominant types of digital attacks. These attacks can handicap sites, organizations, and online administrations, causing huge disturbances and financial misfortunes. Understanding DDoS attacks and how to forestall them is vital for organizations and people to protect their online presence and keep up with operational progression.
Understanding the Basics of DDoS Attacks
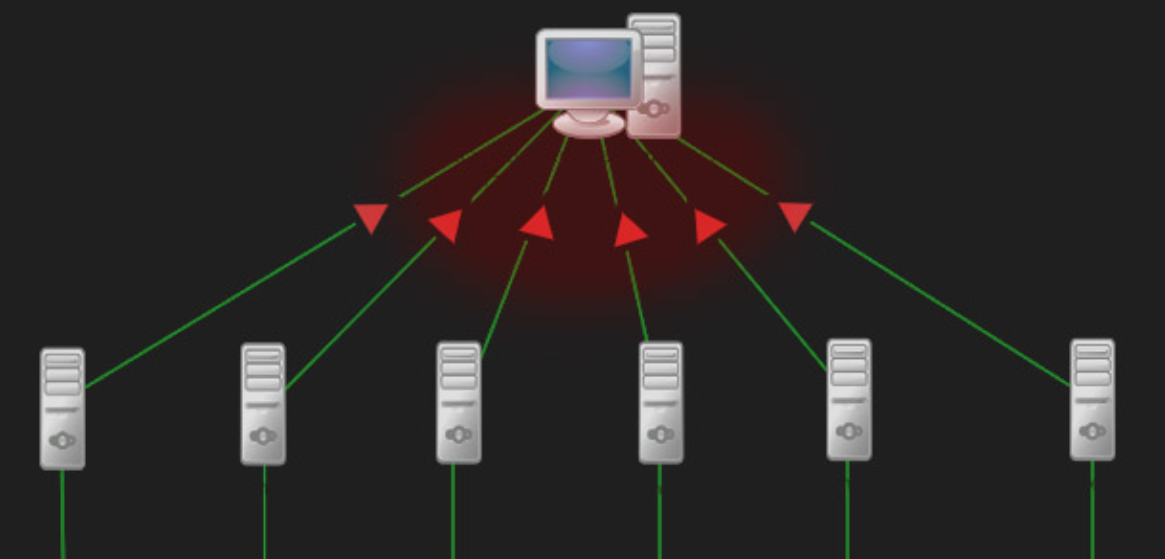
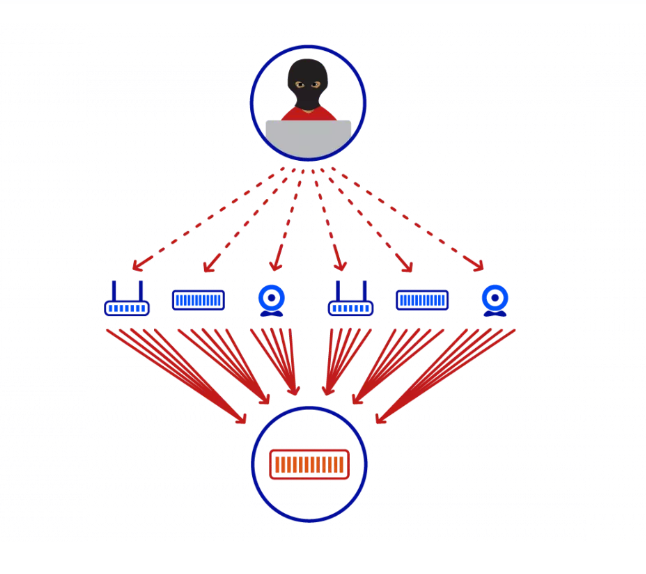
A DDoS (Distributed Denial of Service) attack is a malicious endeavor to upset the typical traffic of a targeted server, administration, or organization by overpowering it with a surge of Web traffic. This sort of digital attack uses the force of numerous compromised PC systems as a source of attack traffic. These can incorporate PCs and other organized assets like IoT devices. Essentially, the attacker takes control of these machines by infecting them with malware, turning them into a botnet – a group of bots used to execute the attack. This makes the attack difficult to counter as it comes from many different sources, thereby distributing the attack across numerous points.
The essence of a DDoS attack lies in its ability to overload the targeted system with excessive requests, to the point where it cannot cope and, as a result, denies service to legitimate users. The scale of these attacks can be immense, with the capacity to send hundreds of gigabits of traffic per second to the victim, far exceeding the bandwidth capacity of most networks. Attacks can target various layers of the network, with some aiming to exhaust server resources (Layer 7 attacks), and others focusing on overwhelming the network infrastructure itself (Layer 3 and 4 attacks).
The refinement of DDoS attacks has developed over time, with assailants constantly developing new techniques to take advantage of weaknesses. In that capacity, these attacks shift in size as well as in the technique, with some utilizing a combination of techniques to upgrade viability and stay away from getting detected. Understanding the essential systems and attributes of DDoS attacks is the most vital step in defending against them, featuring the significance of comprehensive security measures and vigilance in the digital landscape.
The Primary Targets for DDoS Attacks
DDoS attacks are not indiscriminate; they often have very specific targets. These targets are typically high-profile websites or services that play a critical role in their sector or industry. For instance, e-commerce platforms are prime targets due to the significant financial and reputational damage a successful attack can inflict, potentially driving customers away. Financial institutions also fall victim to DDoS attacks, as attackers aim to shake consumer confidence or perhaps even manipulate markets through these aggressive tactics.
Online gaming platforms are another common target. For gamers, any latency or downtime can ruin the gaming experience, making these platforms especially vulnerable to attacks intended to frustrate users. Government and public sector websites are also at risk, not only because of the potential to cause widespread disruption but also as a means of protest or to draw attention to specific political agendas.
Behind each of these targets lies a motivation, whether it’s financial gain, competitive edge, ideological statement, or simply to sow chaos and disruption. Understanding that attackers pick their targets in light of the possible effect of the attack highlights the significance of proactive defense measures.
Organizations and businesses across these areas should perceive the dangers they face and embrace comprehensive techniques to safeguard their online presence from these malignant cyber activities. This includes specialized defenses as well as a more extensive mindfulness and readiness methodology that can adjust to the developing strategies of cyber attackers.
The Motivations Behind Launching DDoS Attacks
The diverse motivations driving perpetrators to execute DDoS attacks are as varied as the attackers themselves. Financial coercion is one critical driver, with attackers requesting money to end or try not to start a surge. These financial requests can injure little to enormous enterprises, utilizing the danger of functional interruption for money-related gain.
Another main thrust is philosophical convictions or activism, frequently alluded to as hacktivism. Gatherings or people use DDoS attacks as a computerized type of protest, focusing on associations or governments to point out political, social, or environmental issues. This type of computerized show expects to upset typical activities to compel discussions or feature complaints on open stages.
Rivalry among organizations can likewise raise DDoS attacks, filling in as a deceitful strategy to sabotage rivals. By knocking a competitor’s online services offline, an attacker can temporarily tilt the market in their favor, potentially diverting traffic and sales to their own or an affiliated business.
Cybercriminals may also deploy DDoS attacks as a smokescreen, a strategic diversion to draw attention and resources away from more insidious activities such as data breaches or financial theft. While an organization scrambles to mitigate a DDoS attack, attackers exploit this chaos to infiltrate systems and extract valuable data undetected.
Revenge or personal vendettas offer another motivation, where individuals target organizations or specific websites to cause disruption and chaos as retribution for perceived wrongs. This type of attack is profoundly private, with the attacker expecting to cause the most extreme interruption and harm to their target.
In synopsis, the inspirations driving sending off DDoS attacks are diverse, including financial benefit, ideological statements, competitive advantage, distraction from further cybercrime, and personal revenge. Understanding these inspirations is essential for associations as they foster methodologies to protect themselves against these problematic cyber threats.
Recognizing the Signs of a DDoS Attack
Identifying the early indicators of a DDoS attack is essential for swift action and limiting potential damage. One of the primary signs is a noticeable slowdown in website performance or an unexpected inability to access the site altogether. This can manifest as prolonged loading times or frequent timeouts, suggesting an abnormal surge in traffic. Additionally, a sudden and unexplained spike in network traffic, significantly above average levels, could indicate that a DDoS attack is underway. Monitoring tools and systems might alert administrators to this unusual activity, prompting further investigation.
Another telltale sign is the intermittent availability of online services. If users report sporadic access issues or if services fluctuate between being available and unavailable without a clear reason, it might be the result of an ongoing DDoS attack attempting to overwhelm the system’s resources. Furthermore, receiving unsolicited notifications or messages demanding a ransom to stop an attack can also be a clear indication that a DDoS attack is not just imminent but actively being used as a leverage tool against the organization.
It’s critical for network and system administrators to remain vigilant and to have in place monitoring systems that can detect these signs early. Implementing a robust incident response plan that includes specific procedures for dealing with suspected DDoS attacks can help mitigate their impact. Early detection paired with a swift and coordinated response can mean the difference between a minor inconvenience and a major disruption to operations.
Essential Steps to Mitigate DDoS Attacks
When an organization finds itself under a DDoS attack, time is of the essence. Quick, decisive actions can greatly reduce the impact of the attack on operations and services. One of the first steps should be to activate a pre-established incident response plan that outlines the procedures for dealing with such cyber threats. Communication is key; ensuring that all relevant parties are informed, including IT staff, stakeholders, and potentially affected customers, can help manage the situation more effectively.
Implementing traffic filtering can help identify and block malicious data packets, a crucial step in mitigating the effects of a DDoS attack. By distinguishing between legitimate and attack traffic, organizations can prevent malicious data from consuming bandwidth and server resources. Employing a combination of blackhole routing and rate limiting can further minimize damage. Blackhole routing diverts and discards attack traffic, while rate limiting controls the amount of traffic allowed to reach the server, ensuring that resources are available for legitimate users.
Increasing network bandwidth might offer a temporary buffer against smaller-scale attacks by accommodating the increased traffic without significant service disruption. However, for more substantial attacks, this alone may not be sufficient. That is where DDoS mitigation services come into play. These particular administrations can absorb and sift through assault traffic before it arrives at the objective organization, utilizing progressed strategies, for example, such as traffic scrubbing to cleanse data streams of malicious content.
Engaging with Internet Service Providers (ISP) or hosting administrations can likewise be useful, as they might offer extra resources or support in moderating the attack. Joint efforts with these substances can once in a while bring about a more organized and powerful defense against the surge.
Ultimately, it’s vital to monitor what is happening, changing protections depending on the situation consistently. DDoS attacks can develop, utilizing various strategies as the attack advances. Remaining careful, adjusting systems continuously, and having an exhaustive comprehension of the network’s ordinary traffic designs are principal in really relieving a DDoS attack.
Implementing Long-term DDoS Prevention Strategies
To proactively combat DDoS attacks, organizations should adopt a multi-layered strategy focused on enhancing their network’s defenses and overall resilience. One critical step is ensuring that all software and systems are regularly updated. By promptly applying security patches and updates, vulnerabilities that attackers could exploit are minimized. This includes not just server software but also operating systems and any applications running on network devices.
Another crucial element involves rigorous security assessments, such as penetration testing. These tests simulate attack scenarios, including potential DDoS attacks, to identify weaknesses within the network infrastructure. Addressing these vulnerabilities before they can be exploited is essential in fortifying an organization’s cyber defenses.
Employee awareness and training form another pillar of long-term prevention. Teaching staff about the meaning of cyber protection and the job they play in keeping up with it helps cultivate a culture of safety. This remembers preparing for perceiving and responding to potential security dangers, the significance of solid secret phrase approaches, and the risks of phishing attempts, which can act as antecedents to additional critical attacks.
Also, utilizing progressed network monitoring tools takes into consideration the constant perception of traffic patterns. These tools can help in the early discovery of irregularities that might show a prospering DDoS attack, empowering speedier response times. Consolidating overt repetitiveness in network arrangements can likewise give flexibility, guaranteeing that assuming one pathway is compromised, others can deal with the traffic load, in thus maintaining service continuity.
Carrying out these systems requires a pledge to cybersecurity as a continuous interaction as opposed to a one-time arrangement. Customary audits and updates to security protocols, related to remaining informed on the most recent digital dangers and cautious advances, will outfit associations with important devices to forestall DDoS attacks and guarantee the security of their online conditions.
The Role of DDoS Protection Services
For organizations that track down the undertaking of continually preparing for DDoS attacks overwhelmingly or those that don’t have the frame of mind to manage such dangers, going to DDoS security administrations can be a distinct advantage. These specific providers offer a hearty safeguard against the surge of DDoS attacks through the use of state-of-the-art innovation and systems.
Traffic scrubbing stands apart as a foundation method utilized by these administrations. It includes sifting approaching traffic to an organization, permitting genuine traffic to go through while blocking malicious data packets related to DDoS attacks. This guarantees that perfect, safe traffic arrives at the organization’s advanced framework, successfully killing the danger without intruding on business tasks.
Besides, DDoS security administrations are continually taken care of with ongoing danger insight, which keeps them a stride in front of attackers. This insight is gathered from a worldwide perspective on creating dangers and is urgent for distinguishing and relieving possible attacks before they can cause hurt. By utilizing such high-level bits of knowledge, these organizations can adjust their protection tools to counter new and advancing attack vectors.
Joining forces with a believed DDoS insurance specialist co-op supports an organization’s cautious stance as well as permits it to zero in on its center business exercises without the steady concern of cyber threats. This joint effort can be especially gainful for associations with restricted network safety assets or those looking to improve their current safety efforts with master support. DDoS security administrations go about as a crucial partner in the continuous fight against digital dangers, providing peace of mind and a safer online environment for businesses and their customers.