An Introduction to Botnets and DDoS Attacks
In today’s digital age, securing internet infrastructure is a top priority for individuals and organizations. The acutest threats to internet security are botnets and distributed denial of service (DDoS) attacks. Cyber terrorism is the use of botnets, such as’ zombie computers,’ to gain control and command of entire networks. These compromised machines can be used to perform a variety of malicious tasks, with the most popular activity being the launching of Distributed Denial of Service attacks.
DDoS attacks are intended to take down the regular traffic of a specific server or service by overwhelming the targeted host with internet traffic. This flood of traffic is usually orchestrated by the botnet, directing a large volume of data from multiple sources to a single target, causing severe disruptions. Such attacks may include congestive DOS attacks that deny the use of sites and other services on the Internet, hence incurring serious operations and financial losses.
More recently, botnets and DDosing have emerged, which also proves the need to discuss this problem in detail and describe how to avoid it. Botnets are formed by cybercriminals and are created when devices are compromised through the use of infected software that exploits underlying software weaknesses or when users are tricked into downloading a dangerous file. Once compromised by hackers, these devices can be used to send spam, steal data, and conduct massive DDoS attacks.
A DDoS attack functions by flooding the target with traffic to cause server crashes while it remains offline for longer periods. Despite such attacks being aimed at business continuity, they also attack users’ privacy and leak their details.
To protect from these threats, it is possible to work on the possibilities of botnets ‘work and DDoS attacks with their possible outcomes. It is feasible that the specifics of such threats and worded messages’ attempts to disseminate them and encourage preventive measures can help safeguard Internet infrastructure from such actions.
Understanding the Functionality of Botnets
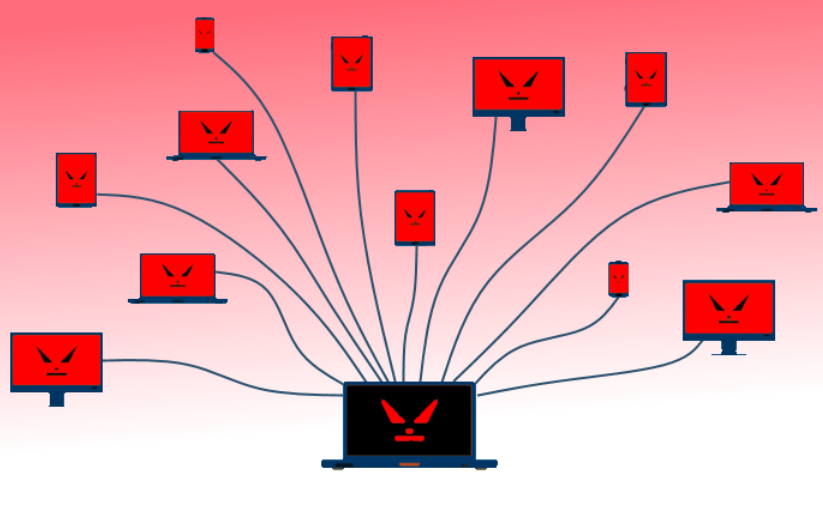
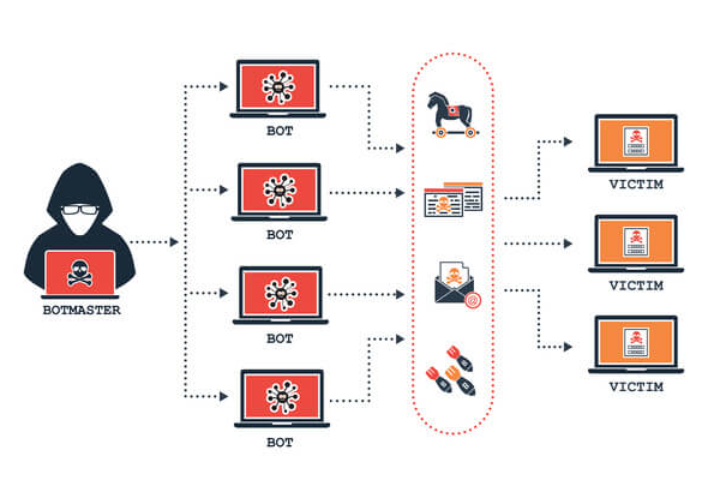
Botnets are networks formed by infecting devices with harmful software, allowing cybercriminals to control them remotely. This infection process is typically covert, exploiting software vulnerabilities or tricking users into downloading dangerous files. Once compromised, a device becomes part of the botnet, often called a “zombie computer.”
These infected devices can be coordinated through a centralized server or a peer-to-peer network. In a centralized setup, a single server issues commands to all the compromised devices. Unlike hierarchical networks that place control in a central point, peer-to-peer networks decentralize control in many nodes, and therefore, it is very hard to dismantle the botnet. Regardless of the control method, criminals can use all these networks to conduct diverse illicit activities.
Unfortunately, one of the botnets’ most well-known applications is to perform “Distributed Denial of Service”, or DDoS for short. In such an attack, the botnet focuses tremendous traffic on a server or computer network. The upshot of this is that the server is overwhelmed with too much data and requires massive processing time; the targeted service becomes unusable and, hence, out of bounds for genuine users for an enormous amount of time.
Alongside DDoS attacks, the botnet may spread spam emails, steal personal information, and distribute other types of malicious software. For instance, a botnet may be used for credential stuffing or for stealing money, identities, or other information from the affected devices. This information can be used for identity theft or sold on the black market, Dr Rooney said.
More recently, the level of botnets has risen, using more elements to avoid being tagged and maintain control of the infected gadgets. Now, some botnets use encryption to protect the traffic with the command and control centre, which becomes difficult for experts to deal with.
This is because modern botnets are rapidly developing and pose a real threat to the security of the internet network. To counter these networks, it is vital to know how they work, with the aim of shielding individual computer users and organizations from their potencies.
The Impact of DDoS Attacks on Internet Security
This is because a DDoS attack can be severe to businesses in several ways, but mainly in terms of financial loss and because the damage is done to the business’s online operations. These scares frequently lead to lost sales since websites and services cease to be available to customers, thus making it almost impossible to maintain business and sales with clients. They do not perceive only monetary losses; a lot is said and done to the companies’ reputations, and the confidence customers place in them. In organizations that depend on digital connectivity, such disruptions threaten long-term organizational relationships and market positions.
The financial implications are compounded by the substantial resources required to defend against DDoS attacks. The current threat level calls for enhanced cybersecurity arrangements, which may be expensive and time-consuming. Control: Protecting against risks is a must with the help of complex fences, IDS, anti-viruses, and other programs; however, these actions cost a lot, including financial and operating costs, so small businesses suffer the most from them.
Like any other internet user, individual users suffer the consequences of DoS/ DDoS attacks. This means that social users can, at one point in time or another, refrain from using their devices, applications as well as websites for payments, communication or any other task. The consequence can mean breaching the privacy of individuals’ lessons if the attackers employ confusion to such an end. It may also mean that those consumers could have their identity cloned and used fraudulently, and this makes consumers afraid to participate in online service offerings again.
It will also impact the rest of the internet organization in general. During their attack, DDoS makes available bandwidth a limited resource, which, in effect, changes the overall business network utilization and can impact many associated services. This results in slow internet speeds and unreliable services for several other services, which will harm both business entities and users.
Furthermore, the constant emergence and high complexity of DDoS attacks make the latter a long-standing problem. The threat constantly evolves, and new tricks are invented to beat current mechanisms. This is why cybersecurity personnel must be alert all the time. Since most of these risks are dynamic, developing sound security solutions to address these ever-changing forms of cyber risks is thus necessary.
The Illegality of Botnets and DDoS Activities
Last, botnets and DDoS attacks are essential cybercrimes that are severely punishable by law. In various nations like the United States, laws such as the Computer Fraud and Abuse Act (CFAA) supply the basis for prosecuting individuals involved in these unlawful dealings. Anyone found involved in botnet or DDoS activities, including those who organize them, stands to lose their property and be imprisoned for several years.
The laws’ goal is not only to punish violators for the current harm caused but also to create a basis whereby potential cybercriminals realize their actions are dangerous and unlawful. This legal regime is also not confined to national jurisdiction, and international cooperation typically assumes an important function in the recognition and prosecution of the offender who might transact in several countries. International bodies like Interpol and Europol work closely with local police to combat continued risks that prevent criminals from getting a clean escape.
Ethically, the operation of botnets and the execution of DDoS attacks severely undermine the trust and functionality of the digital ecosystem. These actions disrupt the rights of users and businesses to receive the availability of trustworthy and protected web services. Such activities break, pry into people’s lives, and in even worse holocaust cases, are dangerous to the general public. The ethical considerations highlight the need to adopt sound regulatory frameworks coupled with practical cybersecurity to protect the sanctity of cyberspace.
Furthermore, the availability and use of botnets, as well as the technical simplicity of DDoS attacks, expose the stability of the internet foundation to considerable danger. Legal measures, therefore, not only penalize but also protect the broader public by aiming to curtail the availability and use of tools and software that facilitate these attacks. This comprehensive approach ensures that internet security’s technical and ethical dimensions are addressed, fostering a safer online space for everyone.
Strategies for Prevention and Protection Against Attacks
A multi-layered approach to security is essential to safeguard against botnet and DDoS attacks. The first is to engage your company in a security audit that helps determine present dangers or gaps in your security systems. Always updating all software and connected hardware helps local networks prevent known exposure to hackers and other cyber threats.
Network management can be well handled with good firewalls and a good intrusion detection system in an organization. It is important to use such tools when looking for features or signs that might be associated with botnet or DDoS attacks. In addition, more efficient rate limiting and traffic filtering reduce these threats even more and limit the incoming traffic.
Another factor that must be implemented is increasing the awareness and training of employees and users. Awareness programs should focus on areas like phishing, password usage and creation, and downloading unknown files. This can go a long way toward decreasing the risks of devices getting hacked.
Companies can engage a reliable cybersecurity firm as their security partner. These firms provide one-off services like risk assessment, attack simulation, reporting, and monitoring. Leveraging their expertise can be invaluable in preventing attacks and minimizing damage if an incident occurs.
Cloud solutions can also provide Customers with more security benefits in terms of solutions. Cloud service providers offer DDoS protection since cloud solutions have more advanced security measures and deeper layers of defence against big-scale attacks than the on-premises infrastructure.
Last but not least, the last element is the creation of a comprehensive incident response plan. This plan must describe the actions to be implemented during an attack, who will take what action, and how the system is to be restored. By responding to such occurrences in the shortest time possible and in unity, a botnet or DDoS attack may be halted as quickly as possible, leaving normal operations to continue unabated.